SS is a command line tool that displays socket statistics and monitor network connections of a Linux system. It has replaced the netstat command which has now been deprecated. The ss command is much faster and prints more detailed network statistics than the netstat command. In this guide, we focus on the how to use ss command to monitor socket connections on a Linux system.
1) View all socket connections (ss)
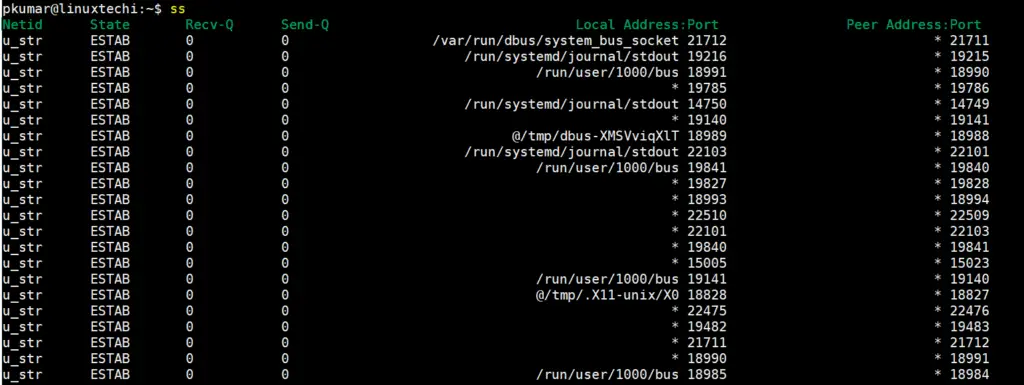
In its basic form, without any arguments, the ss command displays all the socket or network connections (TCP/UDP/UNIX) as shown:
$ ss
To make it easier to view the output, you can pipe the output to less as shown.
$ ss | less
2) View TCP / UDP socket connections
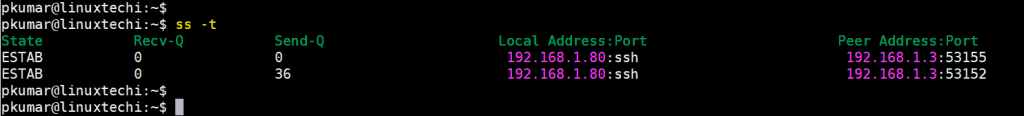
The ss command comes with a myriad of options that you can pass to view different statistics. For example, to view TCP scoket connections only, pass the -t option only as shown.
$ ss -t
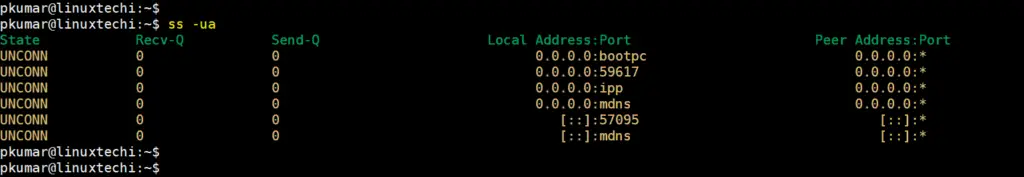
To filter out UDP connections, pass the -ua option as shown.
$ ss -ua
3) View all listening sockets (ss -l)
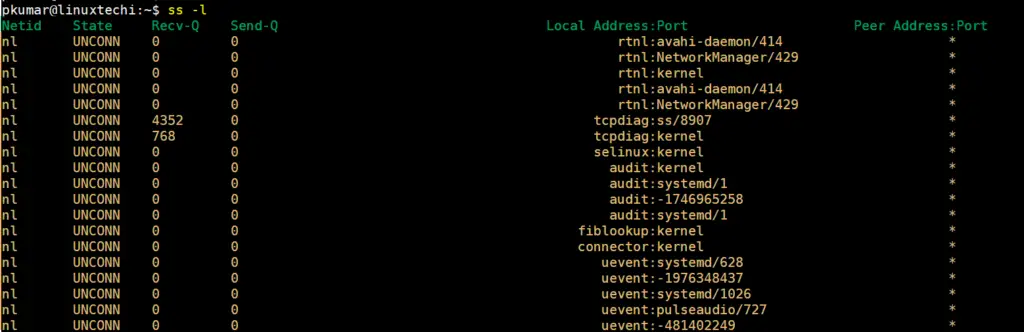
To get a glimpse of all the listening sockets, – which are usually omitted by default, use the -l option.
$ ss -l
4) View all listening TCP socket connections (ss -lt)
To narrow down the search results and list only the TCP listening connections, use the -lt option.
$ ss -lt
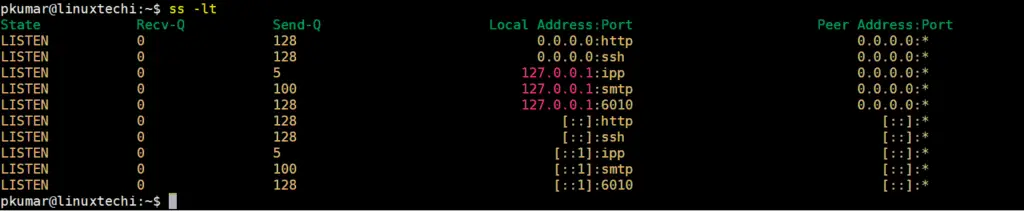
5) View all listening UDP socket connections (ss -lu)
For UDP listening connections, pass the -lu option as shown. In most cases, the listening UDP connections will be fewer than TCP connections
$ ss -lu
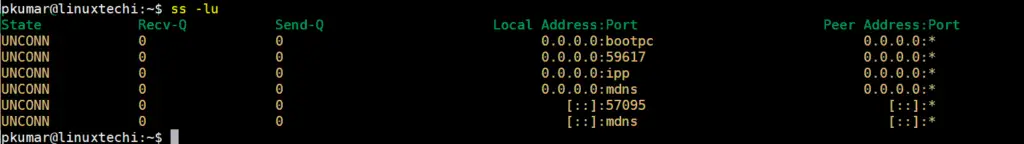
6) View all the listening and non-listening sockets (ss -a)
The -a option will print out all the connected and non-listening sockets on your Linux system as shown.
$ ss -a
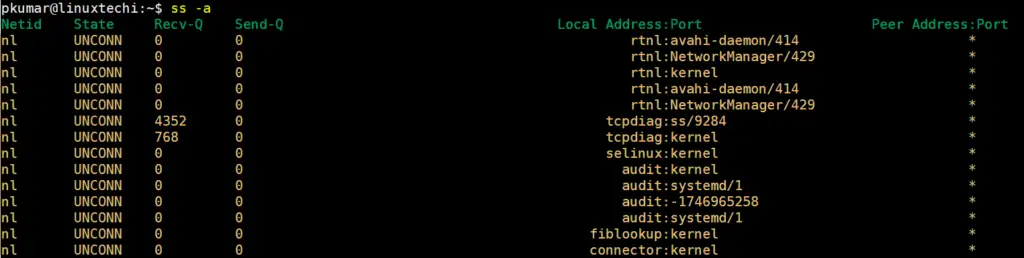
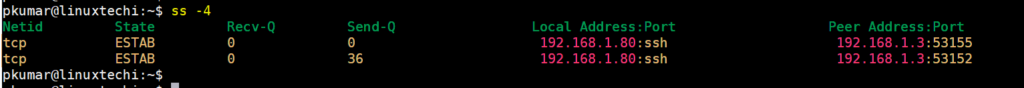
7) List IPv4 and Ipv6 socket connections
To have a peek at the current IPv4 socket connections use the -4 option.
$ ss -4
For IPv6, pass the -6 argument.
pkumar@linuxtechi:~$ ss -6 Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port icmp6 UNCONN 0 0 *:ipv6-icmp *:* pkumar@linuxtechi:~$
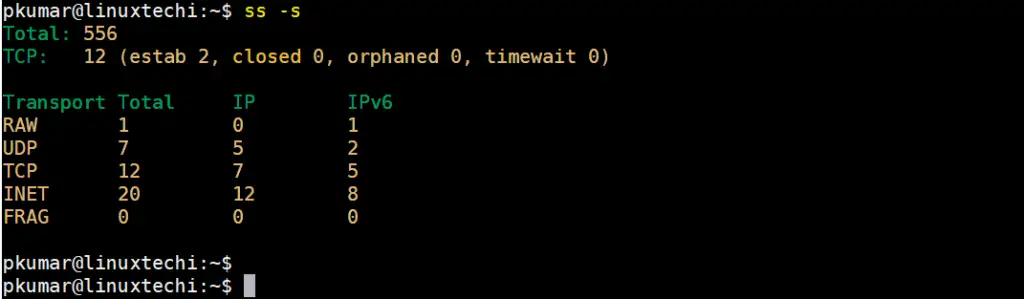
8) List Summary of all socket connections (ss -s)
If you want to just view the overall statistics of the socket connections including the number of TCP & UDP, IPv4 and IPv6 connections simply pass -s option as shown. This prints out the results in a tabular format.
$ ss -s
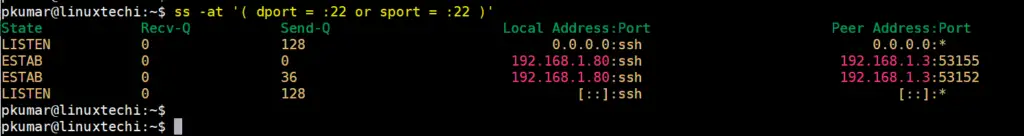
9) Filter connections by port number
You can also decide to filter connections by the port number. For instance, in the example below, we have filtered connections lined to SSH port 22
$ ss -at '( dport = :22 or sport = :22 )'
10) List socket connections without resolving hostname (ss -nt)
By default, ss command tries to resolve ip address into the hostname. In case you want ss command to prevent ip address to hostname resolution then use ‘-n’ option, example is shown below:
pkumar@linuxtechi:~$ ss -nt State Recv-Q Send-Q Local Address:Port Peer Address:Port ESTAB 0 0 192.168.1.80:22 192.168.1.3:53155 ESTAB 0 36 192.168.1.80:22 192.168.1.3:53152 pkumar@linuxtechi:~$
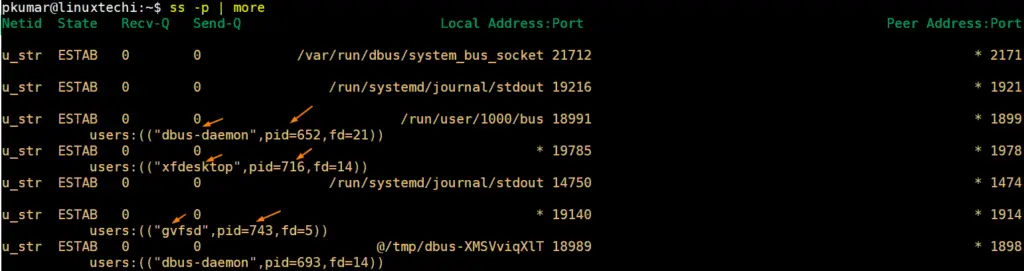
11) List process name and pid for socket connections (ss -p)
Use ‘-p’ option in ss command to list the process name and pid associated to the network connections. Example is shown below,
$ ss -p | more
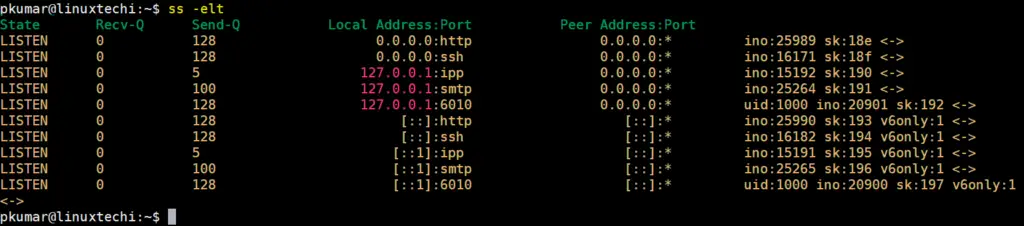
12) Extended output of socket connections (ss -e)
Use ‘-e’ option in ss command to display the extended output of socket connections. Extended output will display the uid of the socket, socket’s inode number and uuid of the socket.
Run below command to list the extended tcp listening sockets.
$ ss -elt
For UDP extended socket connection details, run
$ ss -elu
13) View memory usage of socket connections (ss -m)
Use -m option in ss command to view how much memory is consumed by a socket connection.
Socket memory format would look like below:
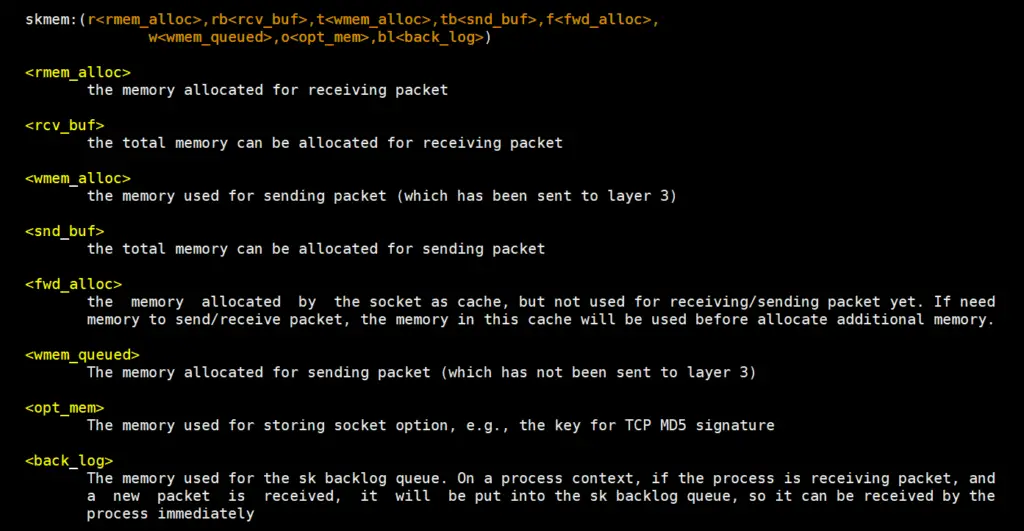
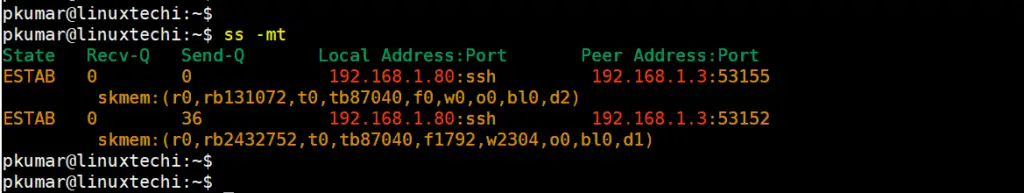
Below command will display the memory usage of tcp connections.
$ ss -mt
14) Kill IPv4 / IPv6 Socket Connection (ss -k)
ss command can terminate or kill ipv4 & ipv6 socket connection forcefully using -k option. Let’s suppose we want to kill ipv4 ssh socket connection.
pkumar@linuxtechi:~$ ss -4 Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port tcp ESTAB 0 0 192.168.1.80:ssh 192.168.1.3:53155 tcp ESTAB 0 36 192.168.1.80:ssh 192.168.1.3:53152 pkumar@linuxtechi:~$
To terminate the 2nd ssh session, use below ss command,
pkumar@linuxtechi:~$ sudo ss -K dst 192.168.1.3 dport = 53152
For more options on the ss command usage, visit the man pages as shown.
$ man ss
This wraps up our guide today. Hopefully, you can now use the ss command confidently to view your socket connections. Thanks for taking your time, and as always, we appreciate your feedback
Also Read : 8 Stat Command Examples in Linux



