OpenDKIM is method to digitally sign & verify emails on the mail servers using public & private keys. In other words opendkim implements the DKIM (DomainKeys Identified Mail) standard for signing and verifying email messages on a per-domain basis. DomainKeys are implemented to reduce the chances of outgoing mails to be marked as SPAM.
In this post we will demonstrate how to install & configure DomainKeys with postfix (MTA) on CentOS 7, i am assuming Postfix is already installed with following domain and hostname.
- Hostname = mail5.freshdaymall.com
- Domain = freshdaymall.com
Also Read : How to install and Configure Postfix Mail Server on CentOS 8
Step:1 Set EPEL Repository using below rpm command
OpenDKIM package is not available in the default yum repositories but available in CentOS 7 EPEL repositories.
[root@mail5 ~]# rpm -Uvh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
Step:2 Install OpenDKIM Package using yum
[root@mail5 ~]# yum install -y opendkim
Step:3 Run below Command to create keys
Execute the below command to create public & private keys under folder “/etc/opendkim/keys”
[root@mail5 ~]# opendkim-default-keygen Generating default DKIM keys: Default DKIM keys for freshdaymall.com created in /etc/opendkim/keys. [root@mail5 ~]# [root@mail5 ~]# cd /etc/opendkim/keys/ [root@mail5 keys]# ll total 8 -rw-r----- 1 root opendkim 891 Nov 29 08:42 default.private -rw-r--r-- 1 root opendkim 320 Nov 29 08:42 default.txt [root@mail5 keys]#
default.private is the private key for the domain and default.txt is public key that we will publish in DNS record (TXT) in the domain. A Selector ( default ) is created while generating keys, a selector can be unique keyword which is associated in keys and included in DKIM signature.
Step:4 Edit the Following Files :
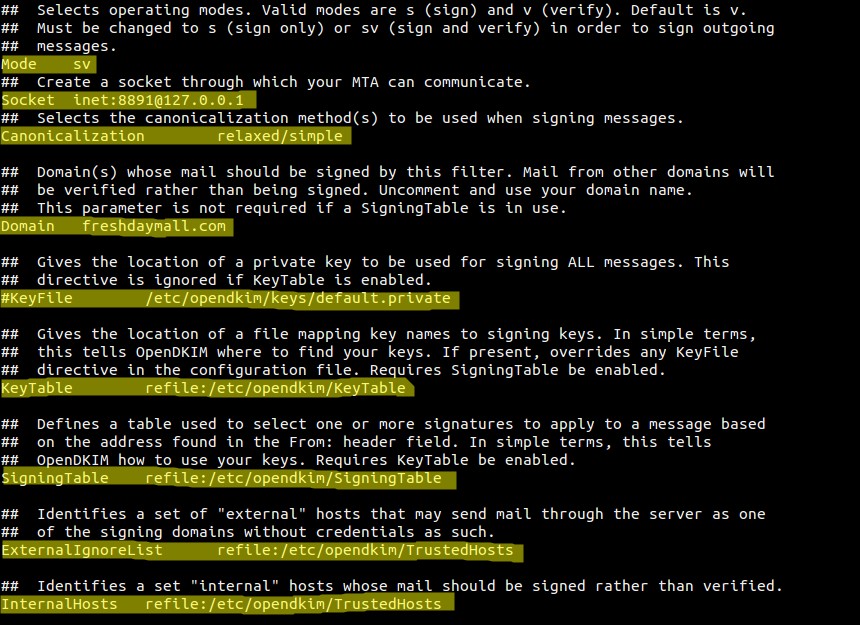
- /etc/opendkim.conf —- Config file of opendkim
- /etc/opendkim/KeyTable —- As name suggest it defines the path of private key for the domain
- /etc/opendkim/SigningTable — This file tells OpenDKIM how to apply the keys.
- /etc/opendkim/TrustedHosts — This file defines which hosts are allowed to use keys.
Edit the file “/etc/opendkim.conf” & set the below parameters.
Edit the KeyTable file and replace the example.com with your domain name.
[root@mail5 ~]# cat /etc/opendkim/KeyTable # OPENDKIM KEY TABLE # To use this file, uncomment the #KeyTable option in /etc/opendkim.conf, # then uncomment the following line and replace example.com with your domain # name, then restart OpenDKIM. Additional keys may be added on separate lines. #default._domainkey.example.com example.com:default:/etc/opendkim/keys/default.private default._domainkey.freshdaymall.com freshdaymall.com:default:/etc/opendkim/keys/default.private [root@mail5 ~]#
Edit the SigningTable file and define who will sign the outgoing mails.
[root@mail5 ~]# cat /etc/opendkim/SigningTable # WILDCARD EXAMPLE # Enables signing for any address on the listed domain(s), but will work only if # "refile:/etc/opendkim/SigningTable" is included in /etc/opendkim.conf. # Create additional lines for additional domains. *@freshdaymall.com default._domainkey.freshdaymall.com
As i am using * in above parameter which means all the users on domain are allowed to sign the emails.
Edit the TrustedHosts file , add Server’s FQDN and domain name below localhost ip (127.0.0.1)
[root@mail5 ~]# cat /etc/opendkim/TrustedHosts # OPENDKIM TRUSTED HOSTS # To use this file, uncomment the #ExternalIgnoreList and/or the #InternalHosts # option in /etc/opendkim.conf then restart OpenDKIM. Additional hosts # may be added on separate lines (IP addresses, hostnames, or CIDR ranges). # The localhost IP (127.0.0.1) should always be the first entry in this file. 127.0.0.1 mail5.freshdaymall.com freshdaymall.com [root@mail5 ~]#
Step:5 Edit Postfix Config File (/etc/postfix/main.cf)
Add the below lines at end of /etc/postfix/main.cf file.
[root@mail5 ~]# vi /etc/postfix/main.cf smtpd_milters = inet:127.0.0.1:8891 non_smtpd_milters = $smtpd_milters milter_default_action = accept
Step:6 Start OpenDKIM & postfix Service
[root@mail5 ~]# hash -r [root@mail5 ~]# systemctl start opendkim ; systemctl enable opendkim ; systemctl restart postfix ln -s '/usr/lib/systemd/system/opendkim.service' '/etc/systemd/system/multi-user.target.wants/opendkim.service' [root@mail5 ~]#
Step:7 Update the TXT DNS record of your domain.
Use the output of default.txt and update the DNS Record (TXT) of the Domain.
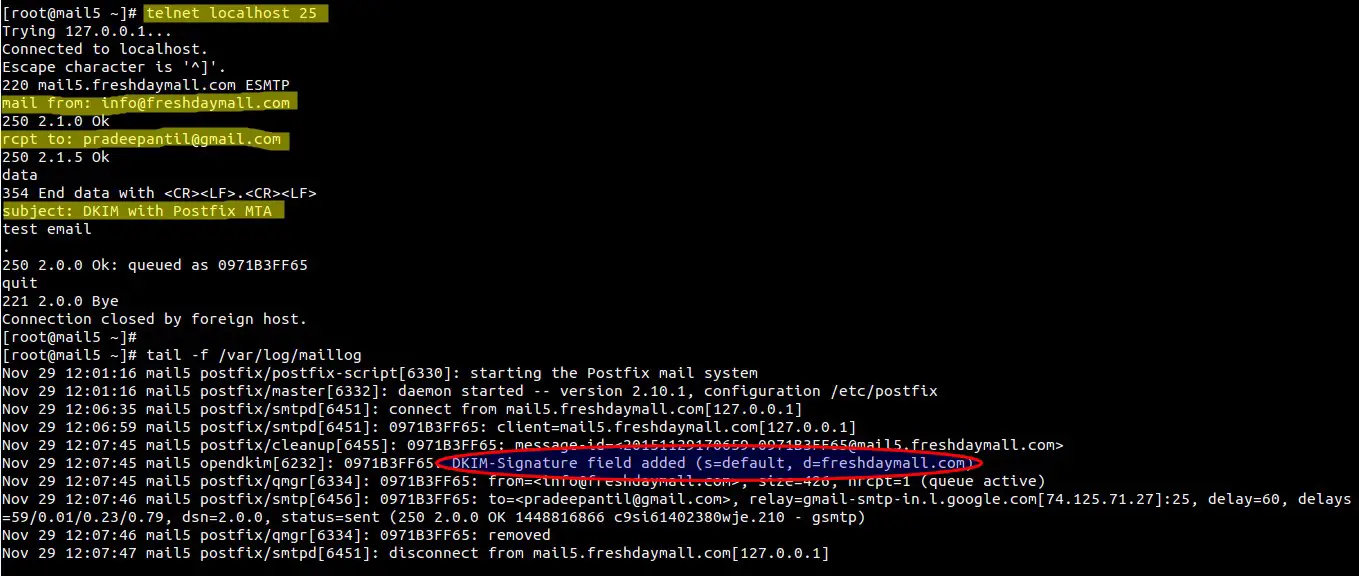
Step:8 Send a Test email and view the logs.
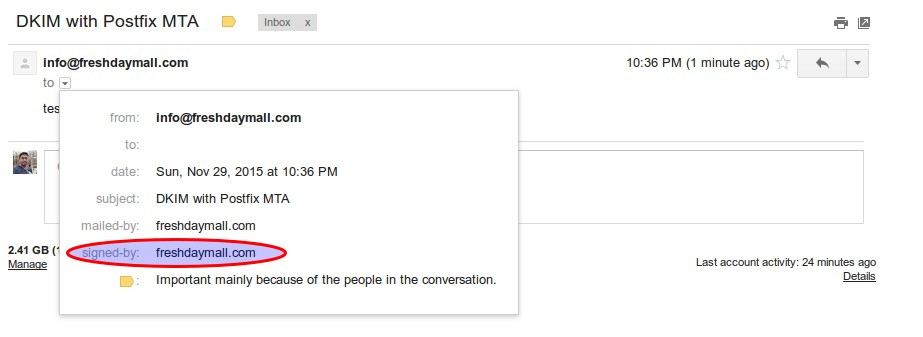
Check whether email is signed or not.
Wow , Our email is signed and domainKeys configuration task is completed now.


What does “hash -r” do? and how can it be installed?
thank you
‘hash -r’ is used to rehash your current shell so that it can locate the opendkim init script.
How do you make a keygen for another domain besides whatever is returned by hostname?
Also, how do you do this for multiple domains?
After entering ‘cat /etc/opendkim/keys/default.txt’ I got a ‘DKIM key default for com’ and not my domain name at the end of the message.
At the start when I ran the command ‘opendkim-default-keygen’, I got a message ‘Default DKIM keys for com created in /etc/opendkim/keys.’ instead of one with my domain name. There isn’t any step defined in your tutorial to change this.
To me, step 3 is incomplete as no domain is being specified here.
Maybe the use of these would be relevant (where mydomain.com is your domain name):
mkdir /etc/opendkim/keys/mydomain.com
opendkim-genkey -D /etc/opendkim/keys/mydomain.com/ -d mydomain.com -s default
chown -R opendkim: /etc/opendkim/keys/mydomain.com
mv /etc/opendkim/keys/mydomain.com/default.private /etc/opendkim/keys/mydomain.com/default
Hi, I got a problem to start openDKIM. It comes out error for “Starting OpenDKIM Milter: opendkim: /etc/opendkim.conf: refile:/etc/opendkim/TrustedHosts: dkimf_db_open(): Permission denied
I try to change permission for 664. It seem not work. Do you have any idea and suggestion for solve this problem?
Changing the group of the key files to opendkim and then giving the group read access fixed that problem for me.
Thanks ! Followed your instructions and it worked straight out of the box.
I am baffled.
I cannot get past your Step 2: “yum install -y opendkim”
I get an error message:
“No package opendkim available”
Do you know why this is happening?
Hi Rodney,
opendkim package is available in the epel repository. So first enable or configure epel repo in your system and then hit the above mentioned yum command.
Hi Thank you,
Clearly, simple, and works great!
I have problem not authenticated but DKIM verification successful and no signing table match for but DKIM verification successful how to fix this problem?
Our web server has a Thawte EV SSL certificate. Should I link to those keys or generate our own opendkim keys? How do I include the IntermediateCA.crt?
this isn’t ssl. they key is simply used by recipients to validate the signature, so it has nothing to do with your ssl key, and since the pubkey is given in dns, there’s no reference to the intermediate CA.